
Banshee 2.0 Malware Exploits Apple’s Encryption to Hide
Apple’s macOS ecosystem, long considered a haven of security, is under threat from a troubling adversary: the Banshee 2.0 Malware. This sophisticated infostealer is leveraging Apple’s own encryption techniques to slip past antivirus programs and wreak havoc on unsuspecting macOS users. First detected in July 2024, this malware has evolved into a stealthy menace that targets browser credentials, cryptocurrency wallets, and even system passwords.
What makes the Banshee 2.0 Malware particularly alarming is its ability to use the same encryption mechanism found in Apple’s XProtect antivirus tool. By adopting this string encryption algorithm, the malware has become nearly invisible to traditional antivirus engines, leaving macOS users vulnerable to cyberattacks.
How Banshee 2.0 Malware Hides in Plain Sight
The key to the Banshee 2.0 Malware’s success lies in its ingenious use of Apple’s encryption. Security researchers at Check Point discovered that the malware mimics the string encryption method used by Apple’s XProtect tool. XProtect, a cornerstone of Apple’s macOS defense system, uses this algorithm to secure its rules for detecting threats.
The malware’s developer, known online as “0xe1” or “kolosain,” appears to have reverse-engineered these encryption techniques to conceal Banshee’s malicious code. This breakthrough allowed the malware to bypass detection by nearly all antivirus tools for months, including the 65 engines listed on VirusTotal.
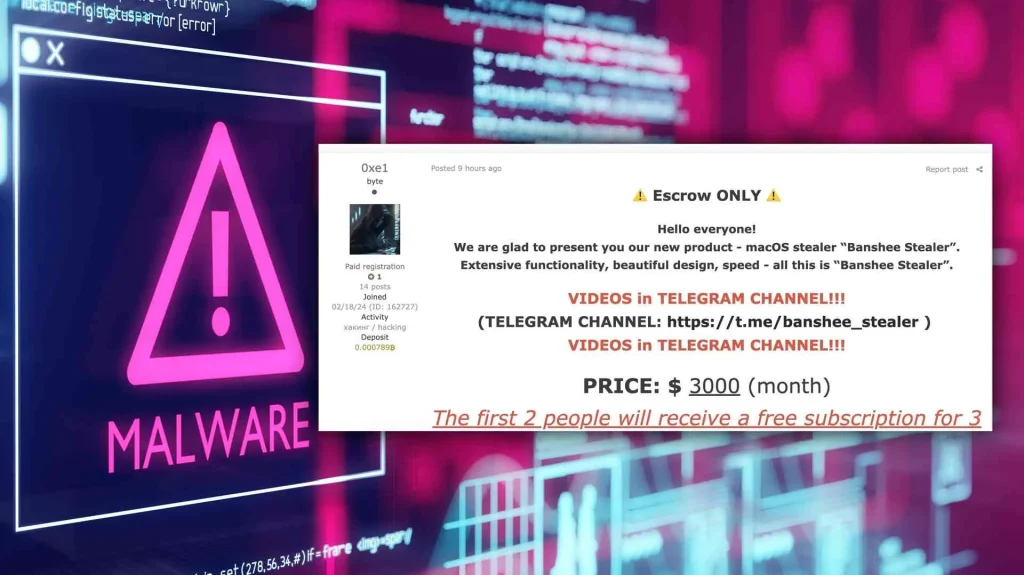
A Dangerous Upgrade for an Old Threat
The original Banshee malware, while effective, was far from perfect. Its code was packaged in plaintext, making it easier for antivirus programs to detect. However, the September 2024 update transformed Banshee into a far more potent version — Banshee 2.0 Malware — by encrypting its strings and dramatically increasing its stealth capabilities.
This upgrade didn’t just make the malware harder to detect; it also expanded its capabilities. The Banshee 2.0 Malware can steal credentials from popular browsers like Google Chrome, Brave, and Opera, as well as cryptocurrency wallet extensions such as Ledger, Exodus, and Guarda. It also collects system data, including software and hardware specifications, and even the password required to unlock the macOS device.
Spreading Through GitHub and Phishing Sites
The Banshee 2.0 Malware has been spreading through two primary methods: GitHub repositories and phishing websites. Between October and November 2024, several campaigns were identified where Banshee was disguised as cracked versions of popular software like Adobe tools and media editing programs. These fake installers, labeled with generic names like “Setup” or “Update,” lured users into downloading the malware.
Phishing websites have been another major distribution channel. These sites mimic legitimate software platforms, offering downloads for apps like TradingView, Parallels, and Telegram. If a visitor is using macOS, they are presented with a malicious download link tailored to infect their system with the Banshee 2.0 Malware.

How the Banshee 2.0 Malware Was Exposed
In November 2024, the source code for the Banshee 2.0 Malware was leaked on a Russian cybercrime forum called “XSS.” This led to the shutdown of the malware-as-a-service (MaaS) operation run by its creator, 0xe1. Despite this, the leaked code has increased the risk of future attacks, as other cybercriminals can now use and modify it.
Antivirus vendors have since incorporated YARA rules to detect the original Banshee malware. However, even after these updates, the encrypted variant of Banshee 2.0 Malware continues to evade detection by many antivirus engines.

Why macOS Users Must Stay Vigilant
The rise of the Banshee 2.0 Malware highlights that macOS is not immune to sophisticated cyber threats. Traditionally viewed as more secure than Windows, macOS is increasingly being targeted by cybercriminals who recognize its growing user base.
The success of the Banshee 2.0 Malware underscores the importance of adopting strong cybersecurity practices. Mac users should avoid downloading cracked software, remain cautious of phishing attempts, and ensure their antivirus tools are up to date.




